Why Moving Identity and Access Management to the Cloud May NOT be a Good Idea
 Today, many organizations are busy transitioning applications to the cloud, and in the process, they are exploring the advantages of as a Service offerings. The “<___> as a Service” concept can apply to a host of different applications and IT functions, including essential business applications such as ERP solutions, email, and content management solutions. Adoption of these services is driven by many factors: a need to be more agile and reduce time to market; directives to reduce IT implementation costs and associated maintenance and support; and external pressures and politics.
Today, many organizations are busy transitioning applications to the cloud, and in the process, they are exploring the advantages of as a Service offerings. The “<___> as a Service” concept can apply to a host of different applications and IT functions, including essential business applications such as ERP solutions, email, and content management solutions. Adoption of these services is driven by many factors: a need to be more agile and reduce time to market; directives to reduce IT implementation costs and associated maintenance and support; and external pressures and politics.
With the expansion of <___> as a Service, many organizations are tempted to also acquire an Identity and Access Management (IAM) solution in the cloud. After all, it seems like it would be easy to subscribe to a service operated by some external entity and call it done.
However, it is important to remember that IAM is a technology that enables you to grant end-user access to both cloud applications and internal applications. This makes it very different from a typical cloud application (e.g., email), which delivers specific, narrow application functionality. Maintaining control of IAM is essential for your organization’s security.
Cloud security can get complex
In the excitement of finding the right cloud applications, it’s easy to overlook (and underestimate) the challenges of integrating those applications with on-premise systems, applications, and infrastructure. One of the most critical integration challenges is how to deliver secure, accurate, and timely access to cloud applications — consistently and strategically.
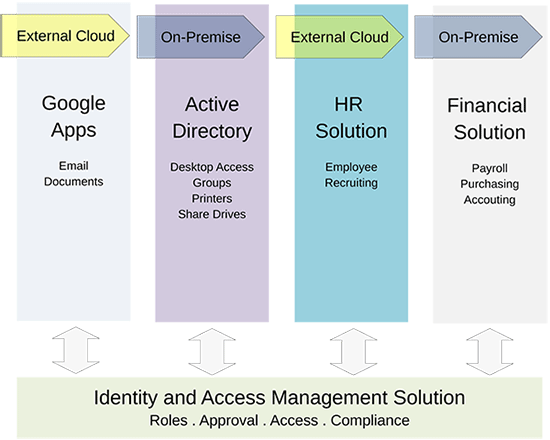
As organizations transition applications to the cloud, many choose a hybrid-cloud solution — that is, a solution that employs both cloud and on-premise applications and systems that co-exist as part of the IT infrastructure. The hybrid cloud has the unintended and often unrecognized consequence of extending an organizations’ security perimeter well beyond the relative “safety” of the internal IT infrastructure environment.
As with so many things in life, the answer lies in knowing (1) where you are and (2) where you are going. Then you can determine the right steps to make sure you reach your destination in the cloud safely!
Where you are — Start by looking at how you currently manage your on-premise identity and access for critical functions such as Active Directory, your badging system, custom applications, and databases. The more formalized your process and the higher the quality of your tools for provisioning end-user access, the better off you are. The inverse is also true: If you use a hodgepodge of scripts and broken business processes that all depend on “tribal-knowledge,” you’re not in a good spot and your organization will likely face big problems when you attempt to secure cloud applications.
Where you are going — For every organization — small or large — if you are heading towards an IT environment in which some applications are in the cloud and some are on-premise, you (yes, YOU!) have to make it all work in real-time. Long gone are the days when you could run “batch jobs” to synchronize data. Today’s operational and security requirements demand real-time access control operations, granting and revoking access at a moment’s notice.
In order to secure the Cloud for your organization, you should urgently consider implementing a robust and formalized approach, and include tools that will enable you to securely, accurately, and quickly grant access for your end users. This is commonly referred to as an Identity and Access Management (IAM) solution.
The need for direct control
Because your IAM solution is integrated with all your applications, both in the cloud and on-premise, it is unique from an operational and security perspective. The approach to IAM and security should obviously be very different from any other type of application.
In short, it makes no sense to treat IAM the way you treat other applications. Instead, you need complete control, operational flexibility, and centralized, robust integration options that allow you to work with disparate systems and solutions in the cloud and on-premise. The solution must be secure, accurate, and timely and be capable of meeting existing and future business and security compliance requirements.
Although IAM as a Service makes sense, consider the unique nature of IAM; then consider implementing your IAM service on premise or with a service or cloud vendor that provides you with complete control and flexibility to deal with all integration options.
Most cloud IAM solutions today don’t even come close to meeting these requirements, but there is hope. Successful strategies and tools do exist.
[cta]For more information about successfully implementing a robust IAM as a Service solution, talk to the experts at Arisant. Contact Joe Wilson, Senior Sales Executive at 303-974-7582 or by email at Joe.wilson@arisant.com.[/cta]

